ATLANTA (PRWEB) January 25, 2019 - NDNB, North America's leading provider of regulatory compliance audits, offers an all new 2019 SOC 2 checklist for download for service organizations seeking to become compliant wit the enhanced SOC framework. Start with a SOC 2 Scoping & Readiness Assessment: Learning about SOC 2 – all the technical merit. Download our SOC 2 Control List Excel Preparing and Implement SOC 2 Controls. Implementing SOC 2 controls can appear overwhelming. Building a robust security program and preforming a SOC 2 readiness assessment can make your team better prepared to go through a security audit and achieve SOC 2 certification. Complimentary user-entity controls: Service organizations would also have to consider if more complimentary user-entity controls would have to be added to Section 3 of the SOC 2 report in relation to privacy. For example, if the service organization is providing services to a hospital, some complimentary user-entity controls could be that the.
SOC 3 Report Example And SOC 2 Controls List can be valuable inspiration for those who seek an image according specific topic, you can find it in this website. Finally all pictures we have been displayed in this website will inspire you all. Download by size: Handphone Tablet Desktop (Original Size) Back To SOC Report Example.
This article was updated in December 2020.
Data is the lifeblood of your business. Your clients must be confident that their information is safe. They trust you to maintain it. If you fail, you will lose your clients' trust.
Reassuring clients is the goal of SOC 2 compliance and certification. The integrity, confidentiality, and privacy of your clients' data are at stake. Potential clients will want proof that you have measures in place to protect them. The SOC 2 compliance audit provides it.
What is SOC 2?
SOC stands for 'System and Organization Controls' and is the agreed upon procedures of controls set by the American Institute of Certified Public Accountants (AICPA).
These defined controls are a series of standards designed to help measure how well a given service organization conducts and regulates its information. They are designed to provide clients confidence that an organization can be trusted to keep their data secure.
The purpose of an audit is to achieve SOC attestation or SOC certification.
Who can perform a SOC 2 audit?
This attestation can only be given after the organization is audited by an independent certified public accountant or CPA Firm who determines if the appropriate safeguards and procedures are in place.
Three Report Types An Organization Can Choose
The first is type 1.
These reports show the service organization's controls over its client's financial reporting standards. The organization being audited defines the objectives that are important to its business, and the controls it follows to achieve those objectives. Since the scope of the audit objective is self-defined, this is a very flexible standard and can be customized to each service provider.
The second is the type 2 report.
Even the switches on the base of the throttle are staggered or separated so telling them apart from feel alone is possible, leaving you free to concentrate on the immersive VR experience. Military-grade Space and Flight Sim PrecisionSaitek introduces the new System. Saitek p990 software. Built to the same exacting standards of Saitek's award-winning Pro Flight range,the X-56 Rhino delivers a multitude of customizable options including all the control surface options required to achieve the exact level ofperformance that aspiring combat pilots demand.The X-56 places controls perfectly under your fingers where subtle distinctions in button feel and shape help you navigate the control set with ease.
It focuses on five trust principals: security, availability, integrity, confidentiality, and privacy. Each trust principal has a standard set of controls and testing criteria for all service providers. When undergoing a Service Organization Control Type 2, the service organization selects which principals are relevant to their business.
The third is the type 3 report.
It is a simplified version of the SOC 2 report and was designed to attest that the service provider has completed a SOC 2 assessment, while also limiting the information to what is relevant to public parties.
SOC 1 and 2 also come in two report types.
Type 1 reports review the policies and procedures that are in operation at a specific moment in time.
The SOC Type II examines the policies and procedures over a period of time no less than six months. Since the Type II report takes into account the historical processes, it is a more accurate and comprehensive audit.
What Is Included in a SOC 2 Certification Report?
What the SOC 2 reports contain depends on the type of service the organization provides.

A service organization can be evaluated on one or more of the following trust services criteria (TSC) categories:
- Security – Information and systems are protected against unauthorized access, unauthorized disclosure of information and damage to systems that could compromise security availability confidentiality, integrity, and privacy of data or systems and affect the entity's ability to meet its objectives.
- Availability – Information and organizational systems are available for operation and use to meet the entity's objective requirements.
- Processing Integrity – System processing is complete, valid, accurate, timely and authorized to meet the entity's objectives.
- Confidentiality – Information designated as confidential is protected to meet the entity's objectives.
- Privacy – Personal information is collected, used, retained, disclosed and disposed of to meet the entity's objectives.
The categories above all share a set of trust services criteria known as the standard criteria.
The common principles are:
- Control environment
- Communication and information
- Risk assessment
- Monitoring activities
- Control activities – which are further broken out by:
- Logical and physical access
- System Operational Effectiveness
- Change Management
- Risk Mitigation
These criteria must be addressed in every SOC audit. Depending on which TSC categories are being assessed, there may be more TSC's which needed to be evaluated in addition to the standard criteria.
With the changes made in 2017, organizations can also get a SOC 2+ report which allows the services organization to address additional criteria from other compliance standards such as HITECH, HIPAA compliance, ISO 27001, Cloud Security Alliance (CSA), NIST 800-53 or COBIT 5.
When you order your compliance audit, you can decide which TSC categories are the most important. Base your decisions on what clients are most likely to want. Doing so will ensure that clients get the information they need. They will be less likely to come back to you with questions if they are addressed in the SOC 2 report.
The key is to reassure clients that you will keep their data secure. Your organizational controls should be explained. That way, clients can be confident that their data is safe with you.
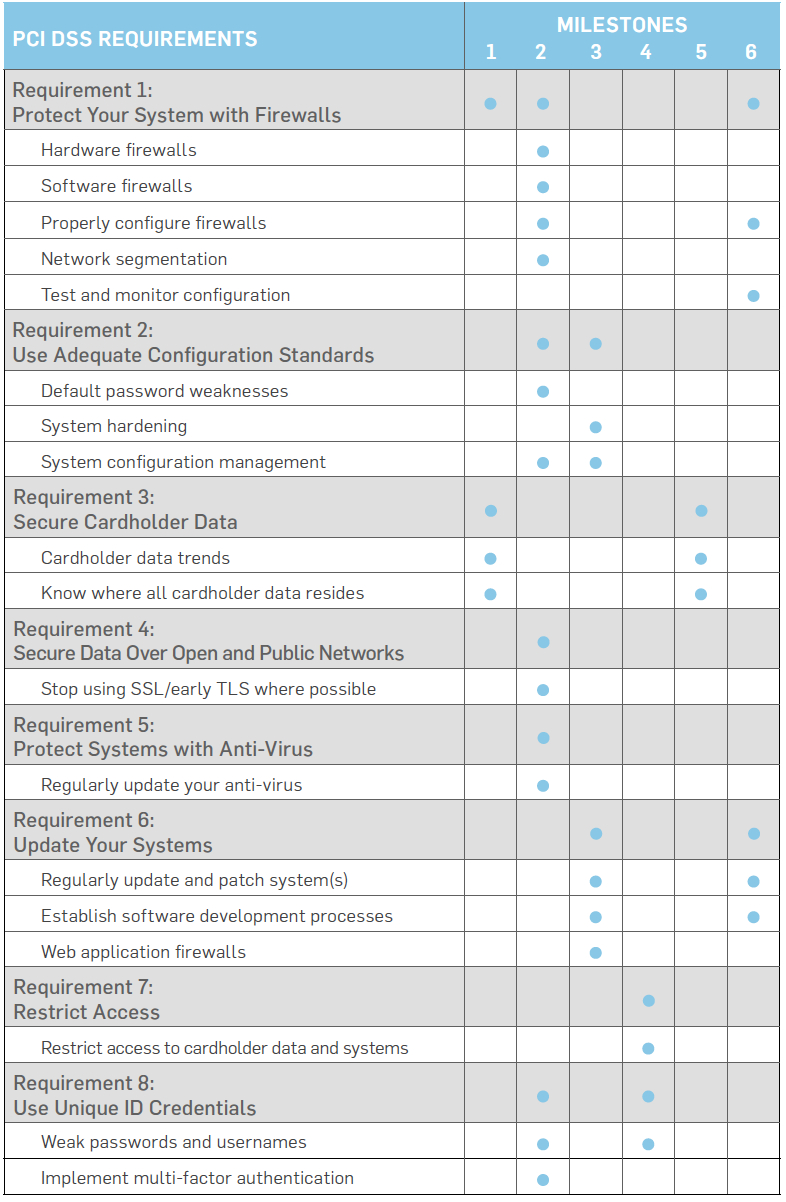
Prepare with a SOC Audit Checklist
There are standard sense steps you can take. Being prepared will make the auditor's job as comfortable as possible.
Your goal is to anticipate issues and try to resolve them beforehand.
Here are six steps you can take to prepare.
Soc Controls List
- Define the operating goals of your audit. You should ask yourself what your clients are most likely to want to know. You know the parameters of the SOC 2 audit. If you handle financial information, you may need a SOC 1 audit, as well.
- Define the scope of your SOC 2 audits. They typically address infrastructure, software, data, risk management, procedures, and people. You will also need to decide which trust principles to include. Any TSC you add will increase the scope of your audit. Again, choose the TSCs that are most likely to concern your clients.
- Address regulatory and compliance requirements. Every industry has regulations. For example, healthcare providers must comply with HIPAA compliance while those handling credit cards require PCI compliance. Doing a review of your enterprise's compliance will help streamline the audit.
- Review and write security procedures. The auditor you hire will use your written policies as a guideline. Many companies fall behind. If your systems are out of date, you should update them. If you lack written procedures for anything covered by the audit, you should create them now. Written policies will help your employees adhere to internal rules.
- Perform a readiness assessment. A readiness assessment is your final chance to prepare. You can do the evaluation yourself. Alternatively, you can hire an auditing firm to do it for you as they abide by strict auditing standards. Think of it as a dress rehearsal. You can use the results to fill in holes in your audit prep.
- Evaluate and hire a certified auditor. As I mentioned before, hire someone with experience in your industry. The auditor will:
- Work with you to choose agreed-upon testing dates
- Give you a list of required documentation in advance of the audit
- Visit your site for document reviews, employee interviews, and walk-throughs
- Document the test results and review any issues with you
- Provide you with a completed type II report to share with your clients
Following these six steps of our SOC 2 compliance checklist will ensure that you have a smooth audit process. It is your job to do as much as you can to prepare. Even if you think your company is in good shape, periodic reviews are a must.
You may want to put a system in place to review written procedures. Doing so on a regular basis will make sure your next audit is without problems.
Who Can Request SOC 2 Compliance Reports?
Any organization contracting with a service provider should be concerned about security. That is true regardless of industry. However, it is not necessary to get a new audit every time.
SOC 1 and SOC 2 reports are meant to be confidential, limited-use documents for the service provider and its customers; however, they were often distributed publicly. The SOC 3 report was created as a result of the growing demand for a public facing report.
Now, any party who is knowledgeable about the services provided may request one. Parties who need to know how the entity's system interacts with others may also get the report. These include user entities, sub-service user organizations, and other parties.
Of course, those interested in the internal controls may also request SOC reports. Before you entrust your data to anyone, requiring a SOC compliance audit is a good idea.
Many companies order SOC 2 audits. Then, they provide a report to prospective clients and other qualified parties.
Of course, it is possible that a client might have questions not covered by the SOC 2 report. In that case, you will need to decide how to respond. The report includes many of the most common questions and concerns clients will have.
How Have SOC Audits Changed?
The standards used for auditing have evolved over the years. Up until 2011, AICPA applied the SAS 70 standard. The SAS 70 standard became extremely popular, and subsequently, it was being used too broadly, and it started to lose the desired focus. In response, AICPA replaced SAS 70 with the Statement on Standards for Attestation Engagements (SSAE) No. 16 in 2011 and recently updated to version SSAE 18, in May of 2017.
The new requirements for the SSAE 18 are as follows.
- IPE, or Information Produced by the Entity. Companies must get evidence of the accuracy of any information provided. Examples might include standard queries or report parameters.
- Vendor management and monitoring of sub-service organizations. Service providers or data centers must include controls for sub-service organizations. The goal is to ensure that anybody with access to the data is adhering to control standards.
- CUECs or Complementary User Entity Controls must be in place. They should be limited to controls that are needed to achieve the stated control objectives
- Internal audit and regulatory examinations. SSAE 18 requires service organizations to read specific reports. Specifically, they relate to internal and regulatory examinations.
The SSAE will continue to evolve as new security risks come to light. Keeping up with risks can feel a bit like a game of Whack-A-Mole.
One example is the new SOC Cybersecurity examination and updated trust services principles that went into effect on December 15th, 2018. AICPA's goal is to stay abreast of information security needs and respond accordingly.
How Much Does SOC 2 Auditing Cost?
The expense can vary depending on what is included.
Some of the things that can affect the cost include:
- The scope of services included in the report
- The TSCs you choose to add
- The size of your organization
- The number of in-scope systems and processes
In other words, if you have multiple systems and methods to include, the price will increase. Any system that affects the security of clients' sensitive data must be audited. That is the only way to reassure clients to trust you with their data.
For the best result, choose a firm with IT auditing experience. They should identify the employees who will complete your audit. It is essential to ensure that the firm does background checks on anyone who will have access to your customer data.
Finally, make sure that you ask for (and check) references before hiring an audit firm. Ideally, the firm you choose should have experience in your industry.
Understand The Importance of SOC Compliance Audits
Compliance with SOC 2 reassures clients. Upon auditing, you can provide them with the reports for their records. Having a current report on hand will ensure that prospective clients know they can trust you. Use our SOC 2 compliance checklist to prepare for an audit.
Recent Posts
SOC 2 is an audit procedure that displays your company's commitment to providing trusted services.
All service providers should be trying to achieve SOC 2 Compliance and Certification. User Entities – i.e., companies that are using your service – want to know you're proactively taking care of their needs.
The guide covers the factors required to achieve SOC 2 Compliance and Certification.
Soc 2 Control Objectives
What is SOC 2?
SOC 2 is part of the AICPA's Service Organization Controls standards based on the AICPA's Trust Service Criteria. First published in 2011, it follows the same format as the SOC 1 Report. However, the AICPA's Assurance Services Executive Committee listed a different set of criteria to be measured for SOC 2 Compliance.
The ‘SOC 2 Report on Controls at a Service Organization' creates a baseline of information safety at a service provider. It is Proof of your organization's compliance will come in the form of a SOC 2 Report. You can think of the User Entity's needs as the risks they're exposed to while they are using your service.
The 5 Trust Principles of SOC 2 Certification
The Trust Service Criteria are defined as principles. Each of the tenets covers an area relating to the safety and control of a user's information. You should keep in mind that a control – such as a software module – could satisfy one or more of the required principles.
Soc 2 Controls List Excel Function
Security
The company should be able to show that their system is protected from unauthorized access. They should also prevent unauthorized disclosure and limit any damage that could influence the availability, integrity, confidentiality, and privacy of the information.
Availability
The system should have controls in place to ensure it's available as needed by the User Entity.
Processing Integrity
Data and information processing should be checked whether they are complete, valid, accurate, timeously executed and authorized.
Confidentiality
Information that is designated as confidential should be protected according to the User Entity's needs.
Privacy
The organization should address the User Entity's needs when they collect, use, retain, disclose and dispose of Personal Information.
Establishing a SOC 2 Compliance Framework
The company's risk assessment determines the framework for SOC 2 Compliance. The risks are based on the type of services provided.
The risk assessment should include the following six steps:
1. Identify the products and services which falls under the SOC 2 Report scope.
2. Evaluate the service process and identify the User Entity's risks.
3. Map the Trust Services to the User Entity's risks.
4. Map the Control Criteria to the Trust Services.
5. Identify gaps in the Control Criteria where Trust Principles are present but not addressed.
6. Map internal user controls to the gaps.
The Scope of SOC 2 Reports
Unlike strict PCI Requirements, it is not required for service providers to cover all 5 Trust Principles in a SOC 2 report. Only those that relate to their activities should be included in the scope. Care should be taken when deciding on which of the TSPs will be in the report.
For services that are outsourced, the supplier will have to show adequate controls are in place at their company's site as part of your report.
Business Processes for the Trust Principle Assessment
The four main areas that are covered during the assessment of the company's TSP Controls are:
Business Policies
Written policies that are relevant to the Trust Principles.
Communicating the System
The company has disclosed its policies to stakeholders and the responsible entities. This includes the users of the system.
Control Procedures
The company has procedures that will achieve the principles set out in the policies.

A service organization can be evaluated on one or more of the following trust services criteria (TSC) categories:
- Security – Information and systems are protected against unauthorized access, unauthorized disclosure of information and damage to systems that could compromise security availability confidentiality, integrity, and privacy of data or systems and affect the entity's ability to meet its objectives.
- Availability – Information and organizational systems are available for operation and use to meet the entity's objective requirements.
- Processing Integrity – System processing is complete, valid, accurate, timely and authorized to meet the entity's objectives.
- Confidentiality – Information designated as confidential is protected to meet the entity's objectives.
- Privacy – Personal information is collected, used, retained, disclosed and disposed of to meet the entity's objectives.
The categories above all share a set of trust services criteria known as the standard criteria.
The common principles are:
- Control environment
- Communication and information
- Risk assessment
- Monitoring activities
- Control activities – which are further broken out by:
- Logical and physical access
- System Operational Effectiveness
- Change Management
- Risk Mitigation
These criteria must be addressed in every SOC audit. Depending on which TSC categories are being assessed, there may be more TSC's which needed to be evaluated in addition to the standard criteria.
With the changes made in 2017, organizations can also get a SOC 2+ report which allows the services organization to address additional criteria from other compliance standards such as HITECH, HIPAA compliance, ISO 27001, Cloud Security Alliance (CSA), NIST 800-53 or COBIT 5.
When you order your compliance audit, you can decide which TSC categories are the most important. Base your decisions on what clients are most likely to want. Doing so will ensure that clients get the information they need. They will be less likely to come back to you with questions if they are addressed in the SOC 2 report.
The key is to reassure clients that you will keep their data secure. Your organizational controls should be explained. That way, clients can be confident that their data is safe with you.
Prepare with a SOC Audit Checklist
There are standard sense steps you can take. Being prepared will make the auditor's job as comfortable as possible.
Your goal is to anticipate issues and try to resolve them beforehand.
Here are six steps you can take to prepare.
Soc Controls List
- Define the operating goals of your audit. You should ask yourself what your clients are most likely to want to know. You know the parameters of the SOC 2 audit. If you handle financial information, you may need a SOC 1 audit, as well.
- Define the scope of your SOC 2 audits. They typically address infrastructure, software, data, risk management, procedures, and people. You will also need to decide which trust principles to include. Any TSC you add will increase the scope of your audit. Again, choose the TSCs that are most likely to concern your clients.
- Address regulatory and compliance requirements. Every industry has regulations. For example, healthcare providers must comply with HIPAA compliance while those handling credit cards require PCI compliance. Doing a review of your enterprise's compliance will help streamline the audit.
- Review and write security procedures. The auditor you hire will use your written policies as a guideline. Many companies fall behind. If your systems are out of date, you should update them. If you lack written procedures for anything covered by the audit, you should create them now. Written policies will help your employees adhere to internal rules.
- Perform a readiness assessment. A readiness assessment is your final chance to prepare. You can do the evaluation yourself. Alternatively, you can hire an auditing firm to do it for you as they abide by strict auditing standards. Think of it as a dress rehearsal. You can use the results to fill in holes in your audit prep.
- Evaluate and hire a certified auditor. As I mentioned before, hire someone with experience in your industry. The auditor will:
- Work with you to choose agreed-upon testing dates
- Give you a list of required documentation in advance of the audit
- Visit your site for document reviews, employee interviews, and walk-throughs
- Document the test results and review any issues with you
- Provide you with a completed type II report to share with your clients
Following these six steps of our SOC 2 compliance checklist will ensure that you have a smooth audit process. It is your job to do as much as you can to prepare. Even if you think your company is in good shape, periodic reviews are a must.
You may want to put a system in place to review written procedures. Doing so on a regular basis will make sure your next audit is without problems.
Who Can Request SOC 2 Compliance Reports?
Any organization contracting with a service provider should be concerned about security. That is true regardless of industry. However, it is not necessary to get a new audit every time.
SOC 1 and SOC 2 reports are meant to be confidential, limited-use documents for the service provider and its customers; however, they were often distributed publicly. The SOC 3 report was created as a result of the growing demand for a public facing report.
Now, any party who is knowledgeable about the services provided may request one. Parties who need to know how the entity's system interacts with others may also get the report. These include user entities, sub-service user organizations, and other parties.
Of course, those interested in the internal controls may also request SOC reports. Before you entrust your data to anyone, requiring a SOC compliance audit is a good idea.
Many companies order SOC 2 audits. Then, they provide a report to prospective clients and other qualified parties.
Of course, it is possible that a client might have questions not covered by the SOC 2 report. In that case, you will need to decide how to respond. The report includes many of the most common questions and concerns clients will have.
How Have SOC Audits Changed?
The standards used for auditing have evolved over the years. Up until 2011, AICPA applied the SAS 70 standard. The SAS 70 standard became extremely popular, and subsequently, it was being used too broadly, and it started to lose the desired focus. In response, AICPA replaced SAS 70 with the Statement on Standards for Attestation Engagements (SSAE) No. 16 in 2011 and recently updated to version SSAE 18, in May of 2017.
The new requirements for the SSAE 18 are as follows.
- IPE, or Information Produced by the Entity. Companies must get evidence of the accuracy of any information provided. Examples might include standard queries or report parameters.
- Vendor management and monitoring of sub-service organizations. Service providers or data centers must include controls for sub-service organizations. The goal is to ensure that anybody with access to the data is adhering to control standards.
- CUECs or Complementary User Entity Controls must be in place. They should be limited to controls that are needed to achieve the stated control objectives
- Internal audit and regulatory examinations. SSAE 18 requires service organizations to read specific reports. Specifically, they relate to internal and regulatory examinations.
The SSAE will continue to evolve as new security risks come to light. Keeping up with risks can feel a bit like a game of Whack-A-Mole.
One example is the new SOC Cybersecurity examination and updated trust services principles that went into effect on December 15th, 2018. AICPA's goal is to stay abreast of information security needs and respond accordingly.
How Much Does SOC 2 Auditing Cost?
The expense can vary depending on what is included.
Some of the things that can affect the cost include:
- The scope of services included in the report
- The TSCs you choose to add
- The size of your organization
- The number of in-scope systems and processes
In other words, if you have multiple systems and methods to include, the price will increase. Any system that affects the security of clients' sensitive data must be audited. That is the only way to reassure clients to trust you with their data.
For the best result, choose a firm with IT auditing experience. They should identify the employees who will complete your audit. It is essential to ensure that the firm does background checks on anyone who will have access to your customer data.
Finally, make sure that you ask for (and check) references before hiring an audit firm. Ideally, the firm you choose should have experience in your industry.
Understand The Importance of SOC Compliance Audits
Compliance with SOC 2 reassures clients. Upon auditing, you can provide them with the reports for their records. Having a current report on hand will ensure that prospective clients know they can trust you. Use our SOC 2 compliance checklist to prepare for an audit.
Recent Posts
SOC 2 is an audit procedure that displays your company's commitment to providing trusted services.
All service providers should be trying to achieve SOC 2 Compliance and Certification. User Entities – i.e., companies that are using your service – want to know you're proactively taking care of their needs.
The guide covers the factors required to achieve SOC 2 Compliance and Certification.
Soc 2 Control Objectives
What is SOC 2?
SOC 2 is part of the AICPA's Service Organization Controls standards based on the AICPA's Trust Service Criteria. First published in 2011, it follows the same format as the SOC 1 Report. However, the AICPA's Assurance Services Executive Committee listed a different set of criteria to be measured for SOC 2 Compliance.
The ‘SOC 2 Report on Controls at a Service Organization' creates a baseline of information safety at a service provider. It is Proof of your organization's compliance will come in the form of a SOC 2 Report. You can think of the User Entity's needs as the risks they're exposed to while they are using your service.
The 5 Trust Principles of SOC 2 Certification
The Trust Service Criteria are defined as principles. Each of the tenets covers an area relating to the safety and control of a user's information. You should keep in mind that a control – such as a software module – could satisfy one or more of the required principles.
Soc 2 Controls List Excel Function
Security
The company should be able to show that their system is protected from unauthorized access. They should also prevent unauthorized disclosure and limit any damage that could influence the availability, integrity, confidentiality, and privacy of the information.
Availability
The system should have controls in place to ensure it's available as needed by the User Entity.
Processing Integrity
Data and information processing should be checked whether they are complete, valid, accurate, timeously executed and authorized.
Confidentiality
Information that is designated as confidential should be protected according to the User Entity's needs.
Privacy
The organization should address the User Entity's needs when they collect, use, retain, disclose and dispose of Personal Information.
Establishing a SOC 2 Compliance Framework
The company's risk assessment determines the framework for SOC 2 Compliance. The risks are based on the type of services provided.
The risk assessment should include the following six steps:
1. Identify the products and services which falls under the SOC 2 Report scope.
2. Evaluate the service process and identify the User Entity's risks.
3. Map the Trust Services to the User Entity's risks.
4. Map the Control Criteria to the Trust Services.
5. Identify gaps in the Control Criteria where Trust Principles are present but not addressed.
6. Map internal user controls to the gaps.
The Scope of SOC 2 Reports
Unlike strict PCI Requirements, it is not required for service providers to cover all 5 Trust Principles in a SOC 2 report. Only those that relate to their activities should be included in the scope. Care should be taken when deciding on which of the TSPs will be in the report.
For services that are outsourced, the supplier will have to show adequate controls are in place at their company's site as part of your report.
Business Processes for the Trust Principle Assessment
The four main areas that are covered during the assessment of the company's TSP Controls are:
Business Policies
Written policies that are relevant to the Trust Principles.
Communicating the System
The company has disclosed its policies to stakeholders and the responsible entities. This includes the users of the system.
Control Procedures
The company has procedures that will achieve the principles set out in the policies.
System Monitoring:
The company monitors the system and takes action to ensure compliance with the policies.
SOC 1 vs. SOC 2 Reports
Two types of SOC reports can be prepared. The type of report your company will need will likely depend on your User Entity's needs. A SOC 1 Report deals with the controls at financial institutions while service-orientated companies prepare a SOC 2 Report.
Type 1 Report
The Type 1 Report records the state of the system at a point in time. This will include a description of the system, a written assertion by management, the designed controls, and the Service Auditor's expressed opinion.
Type 2 Report
A Type 2 report further records the operating effectiveness of the system over a period of time. In addition to the items listed in Type 1, the Type 2 Report will also contain the test results of the system's controls. It uses the 5 Trust Principles to assess the company's risk and how they are managing exposure.
The SOC 2 Reporting Format
The Report has four main sections. Each section covers aspects of the system design, implementation, including whether it is complete and adequate.
Directors Call the System
The description of the system covers details about the services the company offers. It lists the infrastructure (such as hardware and software) that the data processing is done by. Boundaries that relate to these tasks should be recorded.
Additional items to keep in mind as part of the system description: Naruto shippuden episode free english.
- Audit compliance solutions
- Risk assessment processes
- Varied system configurations at different locations
The system description identifies the Trust Service Principles that should be covered. This enables you to map your Control Criteria to them and measure how effective your system is.
Management Provides a Written Assertion
This section contains the assertions made by management regarding the controls they've chosen to use. This is an opportunity to explain each of your methods and the controls that serve the Trust Services Criteria.
If the privacy principle forms part of the report, proof of compliance with the commitments stated in the privacy practice must be shown.
If a subservice is used for any portion of your system, this section should include:
- Details on how information is provided or received from the service provider.
- Controls at the service provider that deals with the handling, processing, maintenance, and storage of information.
Trust Principles that are excluded from the report should be listed along with the reasons why they are not covered.
Design and Operational Effectiveness Details
Section 3 of the SOC 2 Report contains a list of the controls that were designed.
If you are preparing a Type 1 Report, list the designed controls that meet the TSP criteria. For a Type 2 Report, you should include the test results for each of the designed controls. This can be in done in a table format.
To create a suitable control design, your company has to identify the risks that stand in the way of achieving your TSP. You will have to see if your control works as described and make sure there are no other risks that stop you from reaching your TSP.
Expressed Opinion by Service Auditor
The Auditor's opinion will be based on:
Soc Controls Report
- Whether the description of the system was fair.
- If the controls work as they are supposed to (for a Type 2 Report this is done over a period of time).
- If the description presents how the system was designed and built.
- It doesn't leave out or distorts information regarding the system.
- The company complies with its privacy practices (if it was part of the scope).
As part of their opinion, the Service Auditor will list deviations and areas that lack control in the system.
Remember – SOC 2 Certification Creates Trust
When you achieve SOC 2 Compliance and Certification, it will inspire and grow trust in your organization.
User Entities may ask for a SOC 2 Report, and they will specify their TSP needs in the request. In cases like this, the report should be based on their request.
Each Trust Principle covered in the SOC 2 Compliance Report is an opportunity to earn the trust of your clients.
